Mitigating the Risk
In this series, we’ve explored the legal and operational risks of piggy-back tags. We examined Equifax’s 2017 data breach caused by a supply chain attack and looked at the possibility of litigation under the California Consumer Privacy Act. We’ve talked a lot about the risk of third-party tags, but we haven’t talked about mitigating the risk. How do we protect our sites from these malicious attacks?
To prevent piggy-back tags from appearing on your site, you need to know where tags come from and prevent your web pages from communicating with unrecognized domains. A strong Content Security Policy (CSP) filters out web traffic from unrecognized domains, which prevents piggy-backers from getting on your site. Your site's CSP should serve as a whitelist for approved website content. This prevents cross-site scripting (XSS), clickjacking, and other code injection attacks. *Wikipedia ref
You Need Process
There are many sites that help generate a CSP. CSP is Awesome is one example of how to create a CSP for your site. The problem that often happens when managing a CSP is keeping domains up to date without process and automation.
If your Marketing Team adds a new tag, it needs to go into the CSP as part of an onboarding process that your organization closely follows. If a rogue team member inside of your organization tries to add a tag outside of the process, that tag wouldn’t be recognized by the CSP and would be blocked.
The risk is real when a process isn’t followed. Maybe that new campaign won't kick off, or a new feature might not fire, or new content will fail to load. The organization must embrace the process and absolutely must have automation to make sure that the organization can be as agile as it needs to be.
Why Attempts at Process Fail
Maintaining the CSP should not cause business process friction, but it often does. Content Security Policies can be difficult to update regularly. Why is that?
It comes down to communication. The needs of Marketing might warrant a quick update, but IT is usually the one who installs the CSP. Who keeps track? And how?
An Excel spreadsheet in a shared drive might have sufficed in the past. But what happens across many sites, departments, and with many updates? What happens when some tags are slow to load and consequently affect web performance? Then the tag responsibility goes to development.
So, who owns the responsibility for tags? And how do you manage the process?
Unfortunately, and all too often, ownership of the CSP and the Tag Governance discipline falls through the cracks in the organizational silos between IT/Ops, Sec/Ops, and Marketing Teams.
Factoring in Automation
Blue Triangle has a built-in Tag Governance process so users can track what is showing up on their site, when, and how long things are taking to load. Users create alerts for missing tags or services or be notified when new, unexpected services appear. Users also receive alerts when new activities are detected by tags and services. This way everyone stays in the loop, from all departments.
There are three steps in their CSP process. Knowing what is loading on your web pages is the first step.
The next step is approving the domains allowed to communicate with your web pages. Then you can put them in your CSP in different configurations. Since Blue Triangle can track your site’s tags, you can also see the domains they are coming from. Even further, they give you context in your approval process by showing you how often each service is observed on the top six thousand sites on the internet.
The final step is creating the CSP with the Blue Triangle CSP Manager. From there it’s easy to approve or reject domains and then use approved domains to create a CSP.
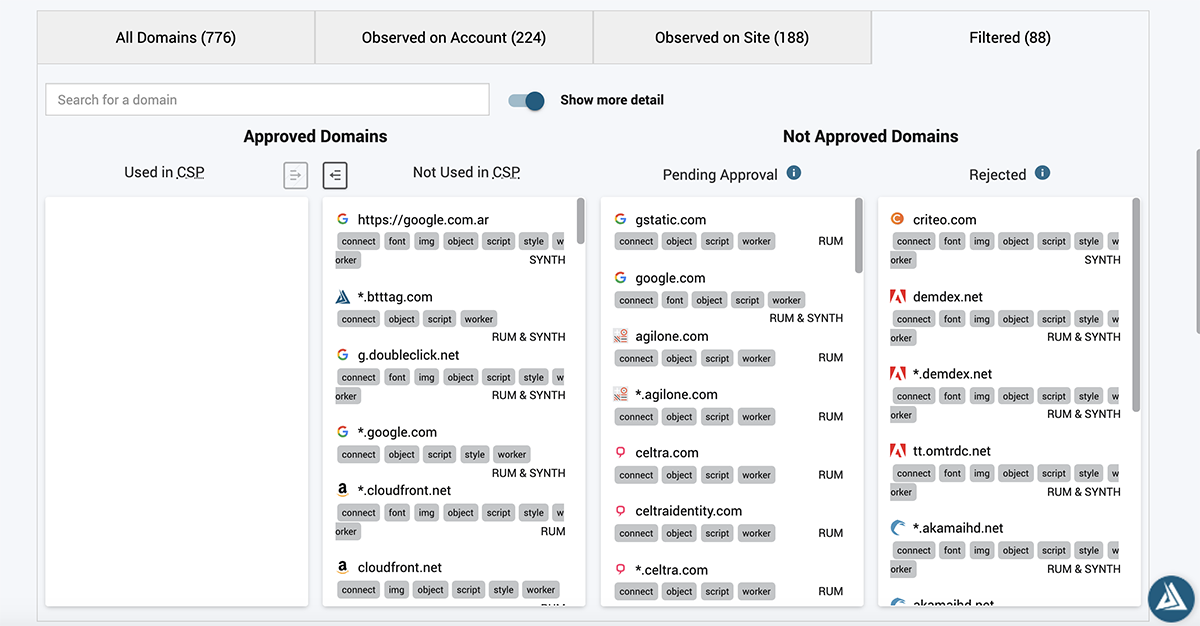
You may want to create different CSP’s for different pages — for example, one for landing pages, a different one for online product pages, and yet another CSP for your checkout process.
Once you have added all the domains you want to include, you can adjust the CSP Directives to tailor the CSP to your needs. Things like disabling or enabled inline JavaScript and CSS are just some examples of the incredible level of control a CSP allows you to have over what code will run on your site.
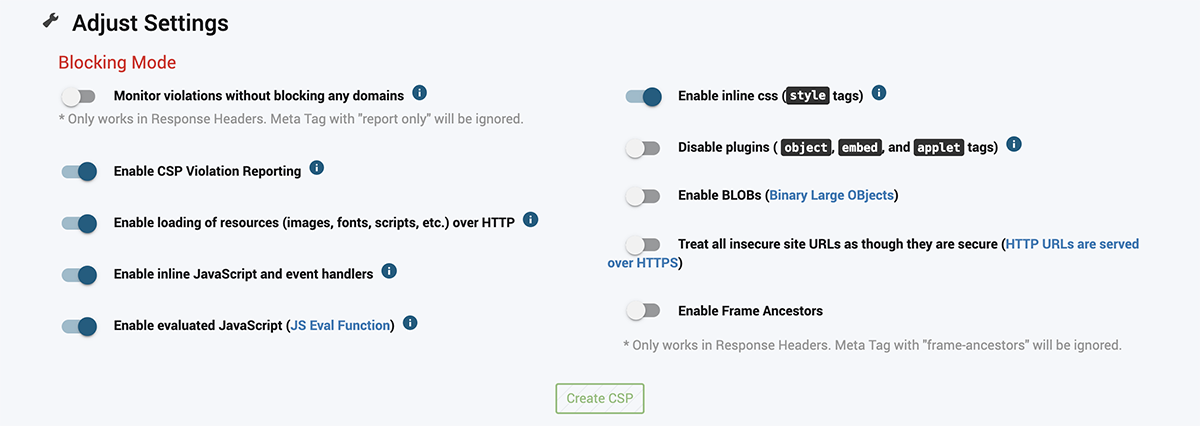
Then save and deploy your CSP with API integrations. You can easily automate the process with whatever level of automation you are comfortable with. After your CSP is deployed, Blue Triangle will continue to track domains, services, and whitelist violations to help monitor the security of your site and your site’s CSP.
So Should You Choose Blue Triangle?
A CSP is the best way to protect your site from piggy-back tags. While Blue Triangle is just one way to create a CSP, their solution helps ease the headache of vetting and monitoring tags as well as creating CSP’s and then maintaining them.
If you’re interested in learning more, I know they would love to help.

During the holiday rush, every shopper matters
Optimize the customer journey before the eCommerce event of the year.

.jpg)

