Myths and legends surround and sometimes obscure what a content security policy (CSP) is and how it can protect your website. The power of a CSP is noteworthy, but it is not an end-all be-all security solution. As an owner of web real estate, you should understand all the advantages a CSP has to offer along with the limitations of what one can protect against.
Rumors on the web are circulating that a CSP is the ultimate in security and can stop all kinds of hacking from Magecart and supply chain attacks to ransomware and malvertisment. While there is some truth in the rumors, many of the claims about a CSP’s effectiveness are hyperbole to get you to buy products and services. You might be asking yourself, “How do I know this isn’t just another fad pandering to panicked business professionals?”
The topic of cyber security is near and dear to me as I once fell victim to data theft. The violation you feel when it happens is real. Now, as a software engineer with over ten years of experience, I have made security a top priority when writing software for all kinds of industries such as healthcare, sciences, government, and retail.
In every space I have worked in, the security of our systems and our customers’ information was always an overarching goal, so I know it is not for lack of trying that most sites get hacked. What many site owners lack is the knowledge they need to prevent breaches from occurring. I am here to educate you so that you can make informed decisions when buying CSP-related software and services to prevent data theft and related malicious attacks.
CSP’s in context
Content security became an issue in 2004 when developers noticed that they could interact with JavaScript that was not in their website’s domain. Unwanted ads, spyware, and pop-ups began plaguing the internet.
To solve the problem, W3C changed the standards for how JavaScript works in a browser by providing different, mutually exclusive contexts for it. However, the contexts retain one common ability: manipulating the Document Object Module (DOM).
The two contexts that JavaScript can live in are the User Level Context, which is under the user’s control, and Site Level Context, which is under the site owner’s control.
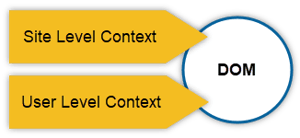
The scripts in each context can NOT interact directly with each other, but they do have the DOM in common, which controls how a site appears to users in a browser.
A CSP controls the JavaScript that can function in the Site Level Context. Rules in the CSP decide which domains can and cannot manipulate scripts in your site’s context. These rules also control which domains can load content for your users.
A CSP cannot control the User Level Context, which exists at the level of a user’s browser. The user gives permission to any script that is running in that context. For example, if a user downloads a Chrome Browser Plugin, they have to activate it before the plugin can function.
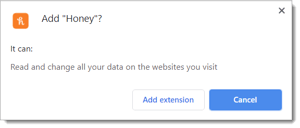
On activation, the plugin must tell the user everything it will manipulate in the DOM, and if the user accepts those terms, that plugin now has all the power to change the DOM at the User Level Context.
Abilities and limitations
Every site on the Internet should have a strong, domain-blocking CSP installed. Without a strong CSP, your site is vulnerable. A site without a CSP is like a bank with an open vault that trusts each visitor to behave and not take things that are not theirs.
A content security policy is your chance to enforce who can and cannot send information to your customers or to anyone else on your behalf. Even a simple CSP can prevent cross-site scripting and other data injection attacks. Cross-site scripting is the main reason why CSP’s were developed in the first place.
The User Level Context will still be able to manipulate the DOM – just not on your behalf. The User Level Context is the reason a CSP does not block third-party plugins from modifying the page. However, a CSP can block those plugins from generating network calls with injected code.
A CSP also blocks attacks that sends customer data out to third parties on your behalf like the infamous Magecart attack. A strong CSP prevents data from being sent from the web page to the criminals and will generate a CSP violation notification in the console log of the page the moment an attempt is made that the CSP blocks.
Data injection is the most common of all attacks on the internet. In fact, data injection attacks are so common that each attack has its own classification. If you set up a strong CSP on your site, most data injection attacks will be blocked automatically, including cross-site scripting (XSS) and clickjacking.
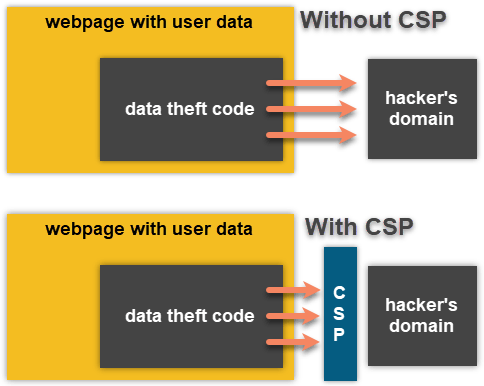
Without a strong CSP, malicious code and data can be injected into your site and send data out, including personal or confidential information. Theft of customer data not only leads to monetary consequences but also erodes customers’ trust. Blocking these kinds of attacks is essential for conducting business on the web, and a CSP is one of the best solutions available.
Other benefits
A good CSP will decide which domains can load content and execute JavaScript on your site. In order to create a good CSP, first- and third-party content must be organized and inventoried so that the content security policy does not block essential content.
While you have to determine what content should be allowed on your site before implementing a CSP, I am not recommending analysis paralysis. Cover your bases and understand which domains regularly load content on your site, or you may inadvertently block important services as you proceed.
On the other hand, accepting every domain that is currently present on your site as a secure source, you may start to lose some of the benefits of having a strong CSP. If you do not scrutinize your services to some level, you may risk including services that are currently compromising your customers’ data.
When a domain inventory is done right, every single tag and piece of content on your site will be accounted for, which can help you recognize what should and should not be on the site. Many sites on the web today have content loading for their customers that is unused, insecure, outdated, or redundant. Removing, updating, or patching this content can create a better user experience.
Better user experience leads to increasing the online revenue stream – a hidden benefit of a strong CSP. Not only can a CSP help you protect your customers. The process of creating a CSP also gives them a better experience which, in turn, leads to stickier customers.
The pros outweigh the cons
Putting a strong CSP on your site can be a windfall, giving you a chance to control the content on your site and securing your customers’ data. We learned that a CSP blocks cross-site scripting (XSS) and injection attacks. We also learned that a CSP cannot block plugin scripts because of the different context levels, but it could help block unwanted network activity if the plugin injected the code onto your web pages. Finally, we learned that a site without a CSP is vulnerable to any of these attacks, and that the site hosting the content is responsible for their customers’ data.
While content management is necessary for having a CSP on a dynamic website, the pros outweigh the cons here, too. A good inventory of your site’s content can lead to better experience for your users. Not only that, but once content is inventoried, you will know what is on your site and why it is there, and management becomes much easier.
Now that you have the knowledge, I hope you can make a more informed decision when buying software that relates to CSP’s. If you are interested in getting your own CSP or have more questions, I invite you to attend one of Blue Triangle’s webinars or view past webinars here.

During the holiday rush, every shopper matters
Optimize the customer journey before the eCommerce event of the year.

.jpg)

