Legal and Operational Risks of Piggyback Tags, Part 1: What the Heck Are They and Why Should I Care?
What Are Tags?
Every business website has “Tags” – they are the pixel or code mechanisms that facilitate the collection and sharing of data between your website and the services you rely on for site analytics and marketing. For example, if you use Criteo for retargeting and Google Analytics for Web Analytics, then Criteo and Google Analytics will each provide a different tag for you as a site owner to place on your website in order to fulfill the services you’ve bought from them.
There are thousands of marketing vendors, and each has their own unique tag. The result is that websites usually have dozens to hundreds of authorized tags that your organization has properly vetted, with each tag performing its own unique tasks related to content, site functionality, sales optimization, and may more categories many of which are collecting data about your site’s visitors on your behalf.
That makes sense. If you’ve bought a service from a vendor, you expect your authorized vendor to gather the data or to perform the functionality that you require.
Where Do Piggyback Tags Come In?
What you almost certainly don’t know is this- your authorized vendors have relationships with other vendors (often, data aggregators). These third-party vendors that you have not authorized also place tags on your site via one of your authorized service tags, which essentially ride “piggyback” on your authorized vendor’s tag.
That third-party, unauthorized tag is called a “Piggyback Tag.”
Yes, you read that correctly. Your authorized vendor is likely allowing unauthorized third-party vendors to attach Piggyback Tags to their tag. Those Piggyback Tags cling to your website like a baby chimp hanging off its mother.
It gets worse. Unlike the baby chimp, Piggyback Tags are not cute.
The third-party, unauthorized vendors also have vendors. And those vendors in turn may also put a Piggyback Tag or two on your site. Imagine that baby chimp hanging on its mom. Now picture a second baby chimp hanging onto the first.
Yep, that’s a Tier 2 Piggyback Tag. Only, the baby chimps are often invisible. It’s not unusual for a website to have hundreds of Piggyback Tags. A large website can easily have thousands.
The Security Risks
Right this minute, as you’re reading this blog post, all of these vendors are creating significant downstream risks for your company because they’re collecting data from your visitors. You almost certainly don’t know:
- Who the vendors are
- Whether their Piggyback Tag is properly maintained
- What data they’re collecting
- How they’re using or selling the data.
- Whether those vendors GDPR or CCPA compliant
What’s more, Piggyback Tag vendors may fail to update or patch their product. As with any software product, updating and patching are essential.
The Risk Applies to Anyone
An unmaintained Piggyback Tag caused one of Equifax’s 2017 data breaches: criminals exploited an unpatched, vulnerable Piggyback Tag attached to its website and used it as a back door into Equifax’s data (this is also known as a “Supply Chain Attack”).
According to Equifax's Statement for the Record, hackers stole "names, Social Security numbers, birth dates, addresses, and in some instances, driver’s license numbers. In addition, credit card numbers for approximately 209,000 consumers and certain dispute documents, which included personal identifying information, for approximately 182,000 consumers were accessed."
Equifax CEO, Richard Smith, lost his job and the company’s reputation sustained painful damage. Here’s what happened to its share price:
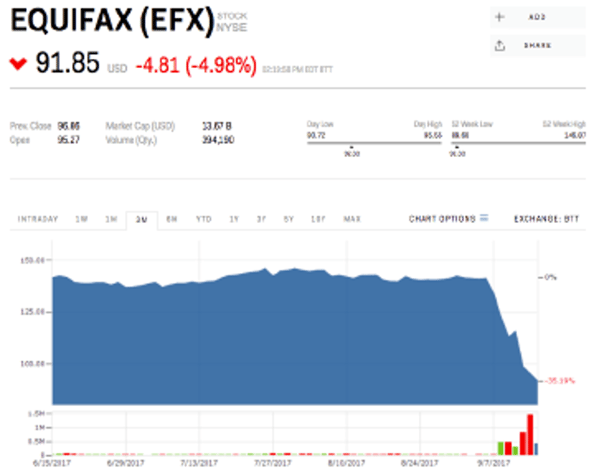
Equifax was one example of a vulnerability that hackers can exploit to insert code either directly onto a website’s first party code or from the code of numerous 3rd parties.
Why Vetting All Tags Is Essential
Keep in mind that each trusted third-party vendor you add to the site carries risk, which you can partially mitigate with careful vetting.
The risk goes up exponentially as third-party vendors add additional vendor services you have not authorized - AKA Piggyback Tags that your organization has not been able to vet for vulnerabilities. But without control or knowledge of the content that loads on your site, one of your vendors could add a Piggyback Tag at any time outside of your knowledge or approval.
That's a huge security risk. In Part 2 of this series, the privacy risks for your users and what that means for your site will be covered.
What You Can Do
So what actions can you take to prevent unauthorized third-party content on your site, and only allow third-parties to place content on your site that you have already vetted?
The adherence to a well implemented Tag Governance process as well as a properly implemented Content Security Policy (CSP) can effectively prevent unauthorized third-parties and the inherent risks they represent.
PART 2: Piggyback Tags and the California Consumer Protection Act >>>

During the holiday rush, every shopper matters
Optimize the customer journey before the eCommerce event of the year.

.jpg)

